${VAR:default} syntax for environment variable injection. If environment variables are not set, default values will be used.
A common practice is to inject through different .env, .env.development, .env.prod files, though you can also directly modify the configuration to hardcode a value.
Basic Configuration
The PID here should be consistent with the PIDs mentioned below, used for service management and hot reload functionality.
Storage Configuration
The storage configuration module is mainly used to store gateway proxy configuration information. Currently supports two storage methods:db storage
Store in database, each configuration is a record, supports SQLite3, PostgreSQL, MySQL
api storage
Store configurations through API endpoints, allowing for external configuration management systems
Configuration Example
Notification Configuration
The notification configuration module is mainly used to letmcp-gateway detect updates and perform hot reloads without restarting the service when configuration updates occur.
Supported Notification Methods
signal
Notify by sending operating system signals, similar to
kill -SIGHUP <pid> or nginx -s reloadapi
Notify by calling an API,
mcp-gateway will listen on an independent portredis
Notify through redis publish/subscribe functionality, suitable for single machine or cluster deployment
composite
Composite notification, combining multiple methods,
signal and api are always enabled by defaultNotification Role Description
sender
sender
Responsible for sending notifications,
apiserver can only use this modereceiver
receiver
Responsible for receiving notifications, standalone
mcp-gateway is recommended to use only this modeboth
both
Both sender and receiver, cluster deployed
mcp-gateway can use this approachConfiguration Example
Session Storage Configuration
Session storage configuration is used to store session information in MCP. Different storage methods can be chosen based on different deployment scenarios:memory storage
Memory storage, suitable for single machine deployment (note: restart will lose session information)
redis storage
Redis storage, suitable for single machine or cluster deployment, supports persistence
Configuration Example
Forward Headers Configuration
The forward headers configuration allows the MCP Gateway to forward HTTP headers from client requests to downstream services. This feature is useful for authentication, request tracing, and custom header propagation.Forward headers functionality is disabled by default for backward compatibility. Enable it by setting
enabled: true in the configuration.Features
Header Filtering
Control which headers are forwarded using allow/ignore lists with case-insensitive matching
Client Headers
Forward headers from client requests (tools/list and tools/call) to downstream services
Argument Headers
Support forwarding headers passed as tool arguments via configurable parameter names
Override Control
Choose whether to override existing headers or add to them
Configuration Options
Header Filtering Logic
The filtering logic follows a priority-based approach:Priority Check
If
allow_headers is configured (non-empty), it takes priority and ignore_headers is completely ignoredAllow List Mode
When
allow_headers is set, only headers in this list are forwarded, all others are ignoredIgnore List Mode
When
allow_headers is empty, headers in ignore_headers list are filtered out, others are forwardedUsage Examples
Example 1: Allow Only Specific Headers
Authorization, X-API-Key, and X-Request-ID headers are forwarded.
Example 2: Block Specific Headers
Accept, Host, Cookie, and User-Agent are forwarded.
Example 3: Tool Argument Headers
custom_headers argument:
Environment Variables
All forward headers settings can be configured via environment variables:Tracing (OpenTelemetry → Jaeger)
MCP Gateway supports distributed tracing via OpenTelemetry and exports to Jaeger. This is optional and disabled by default.What You Get
- Inbound HTTP requests are traced via Gin instrumentation (health check is excluded)
- Downstream HTTP calls propagate trace context automatically
- Optional capture of downstream request fields/body and error previews for faster debugging
Configuration
Environment Variables
Local Jaeger
- Use the provided compose file to start Jaeger locally:
deploy/docker/jaeger/docker-compose.yml - Command:
docker compose -f deploy/docker/jaeger/docker-compose.yml up - Jaeger UI: http://localhost:16686
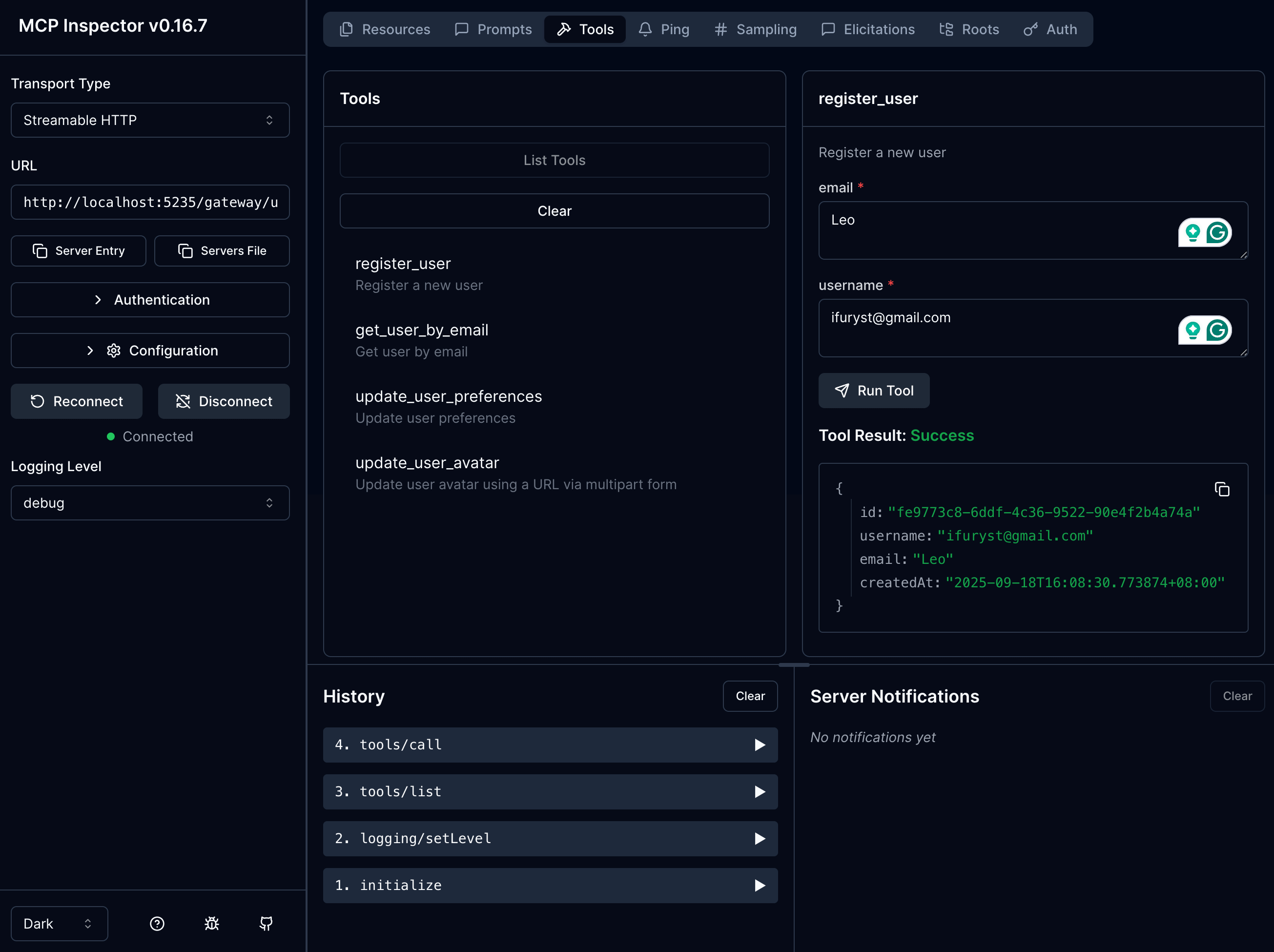
Screenshots
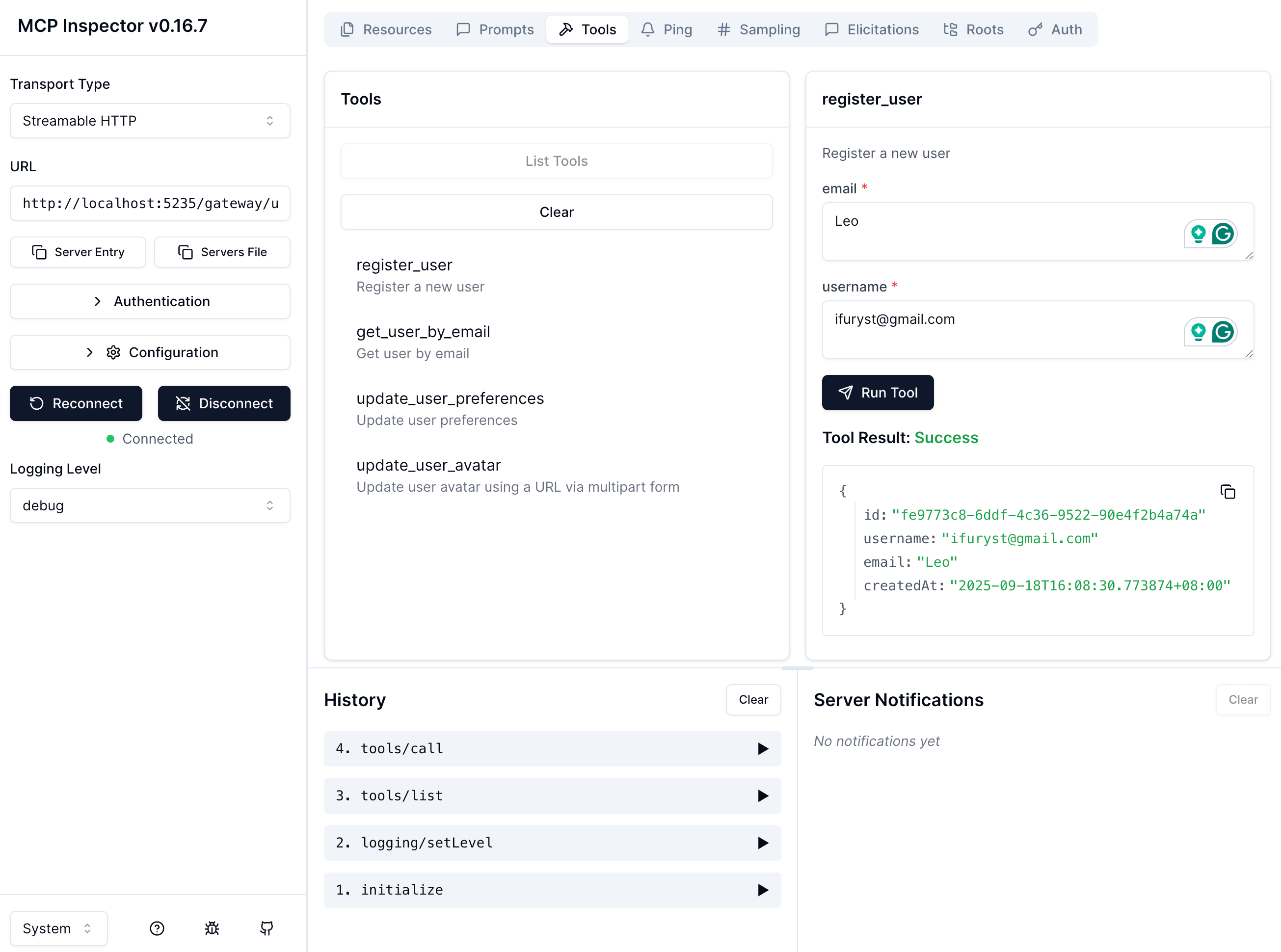
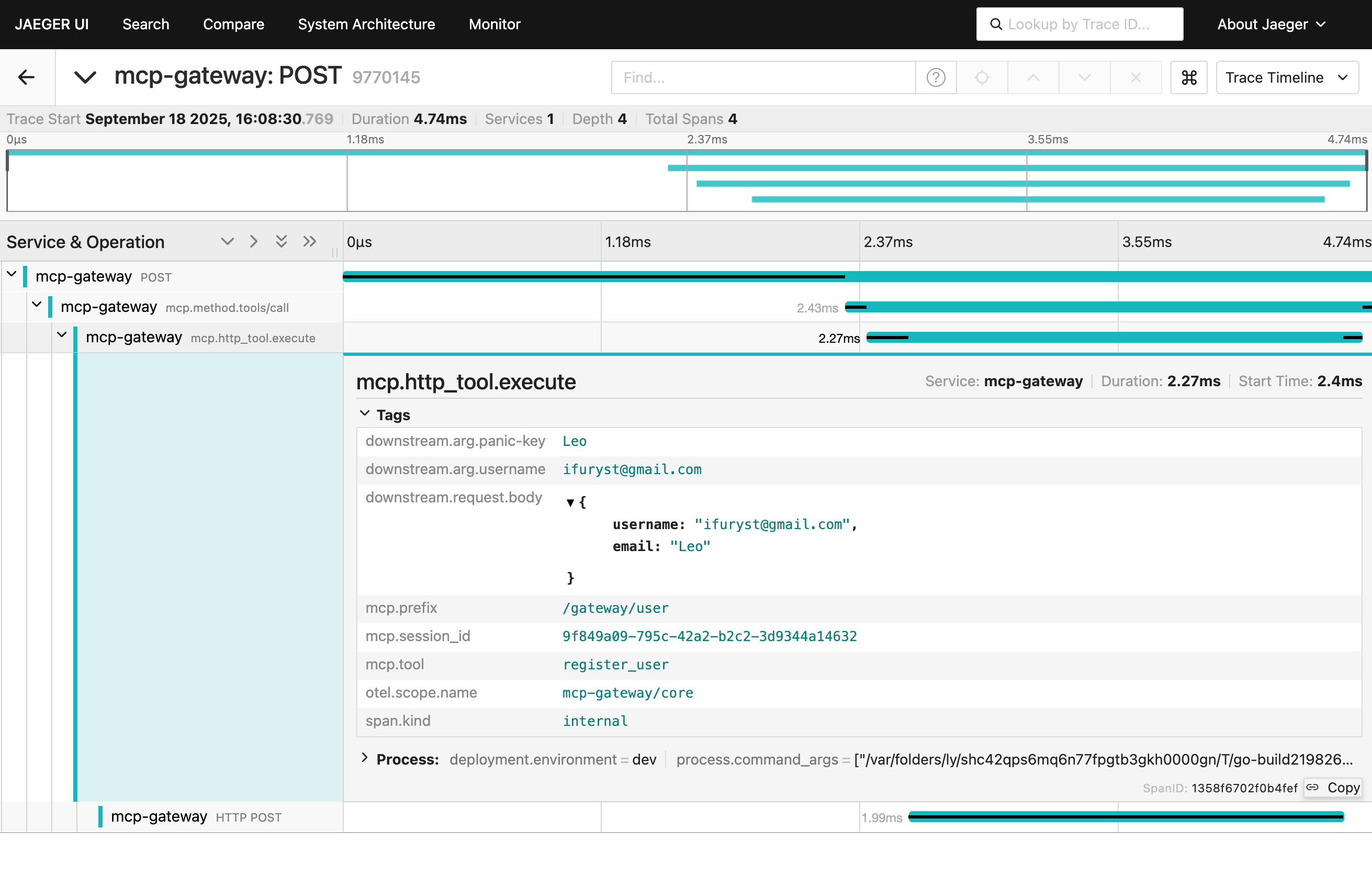
Configuration File Location
By default, configuration files should be placed in the following locations:- Container deployment:
/app/configs/mcp-gateway.yaml - Binary deployment:
./configs/mcp-gateway.yaml
Hot Reload Mechanism
MCP Gateway supports hot reload configuration, allowing new configurations to be applied without restarting the service:Configuration Update Detection
When configuration changes occur, reload is triggered through configured notification methods (signal, api, redis)
Configuration Validation
Before reloading, the validity of the new configuration is verified to ensure stable service operation
Best Practices
Single Machine Deployment
Single Machine Deployment
- Recommended storage type:
dbwith SQLite - Notification type:
compositeorsignal - Session storage:
memoryorredis
Cluster Deployment
Cluster Deployment
- Storage type:
dbwith PostgreSQL or MySQL - Notification type:
redisorcomposite - Session storage: recommended
redis
Production Environment
Production Environment
- Use strong passwords to protect Redis and database
- Regularly backup configuration data
- Monitor service health status and performance metrics